
Picture this: It’s 2025, and a digital lender wakes up to find hundreds of fraudulent loan applications pouring in from unknown IP addresses. Their internal team scrambles to halt disbursements, but the damage is already done, funds and customer trust are on the line. If this scenario sounds dramatic, that’s because in the lending world, threats can escalate overnight. The good news? Implementing the right security features helps you sleep easier, knowing your platform is well-defended against emerging threats.
Below, you’ll find ten must-have security elements that form a solid blueprint for digital lending success, balancing protection, compliance, and user experience so you don’t have to compromise on growth.
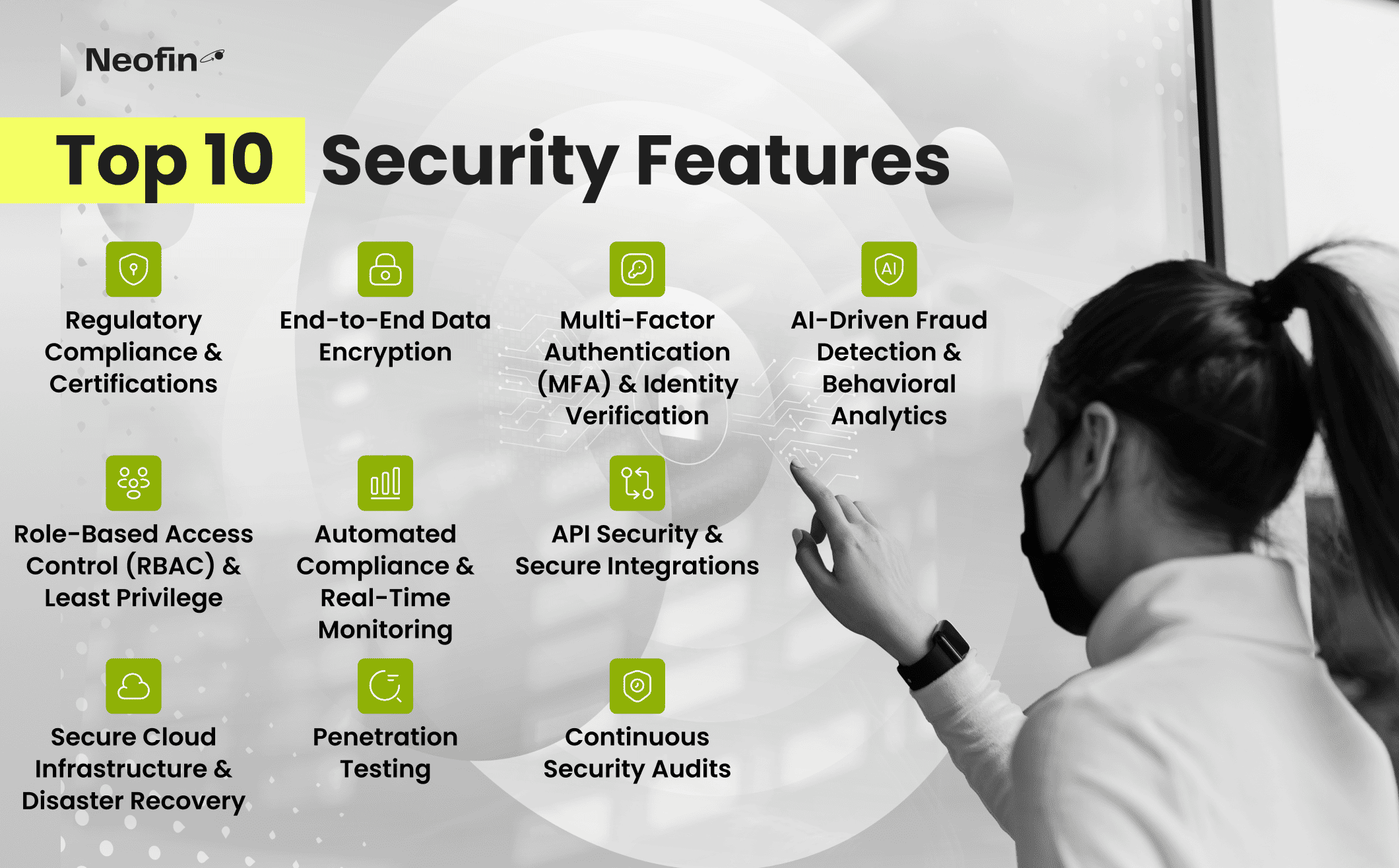
Security Feature #1: Regulatory Compliance & Certifications
Compliance is the foundation of trust in lending. A secure platform must not only meet global and regional standards but also proactively adapt to evolving regulations.
Global and regional regulations for financial services are expanding rapidly, and non-compliance can lead to hefty fines and reputational damage. Adhering to internationally recognized security standards is the baseline for any serious lending platform.
At Neofin, we divide all the security features into global and regional compliance standards.
Global Standards
ISO 27001: The gold standard for information security management.
SOC 2: Ensures safe handling of sensitive data, particularly crucial for financial operations.
PCI DSS: Mandates secure payment data handling, especially relevant for lenders facilitating transactions online.
Regional Compliance Specifics
Europe (EU & UK): GDPR imposes strict data handling rules; PSD2 and Open Banking require secure APIs; AML Directives crack down on money laundering.
United States: CCPA grants consumers control over personal data; FCRA enforces fair credit reporting and anti-discriminatory lending.
Middle East: DIFC Data Protection Law (UAE) mirrors GDPR principles; Saudi Central Bank (SAMA) regulations demand rigorous KYC controls; Shariah-compliant lending adds unique obligations for Islamic finance.
Maintains ISO 27001, SOC 2, and GDPR compliance with annual status confirmations and audits.
Undergoes quarterly ASV scans by external vendors to identify and fix vulnerabilities.
Executes yearly policy reviews through independent auditors, ensuring alignment with new regulations and industry best practices.
Offers pre-entry compliance support to help clients meet local requirements before launching in new markets.
In an era where data breaches can cost companies millions and irreparably damage trust, end-to-end encryption is non-negotiable, especially in security lending. Whether dealing with securities lending income or executing securities lending transactions, data at rest and in transit must be fully encrypted to prevent unauthorized access.
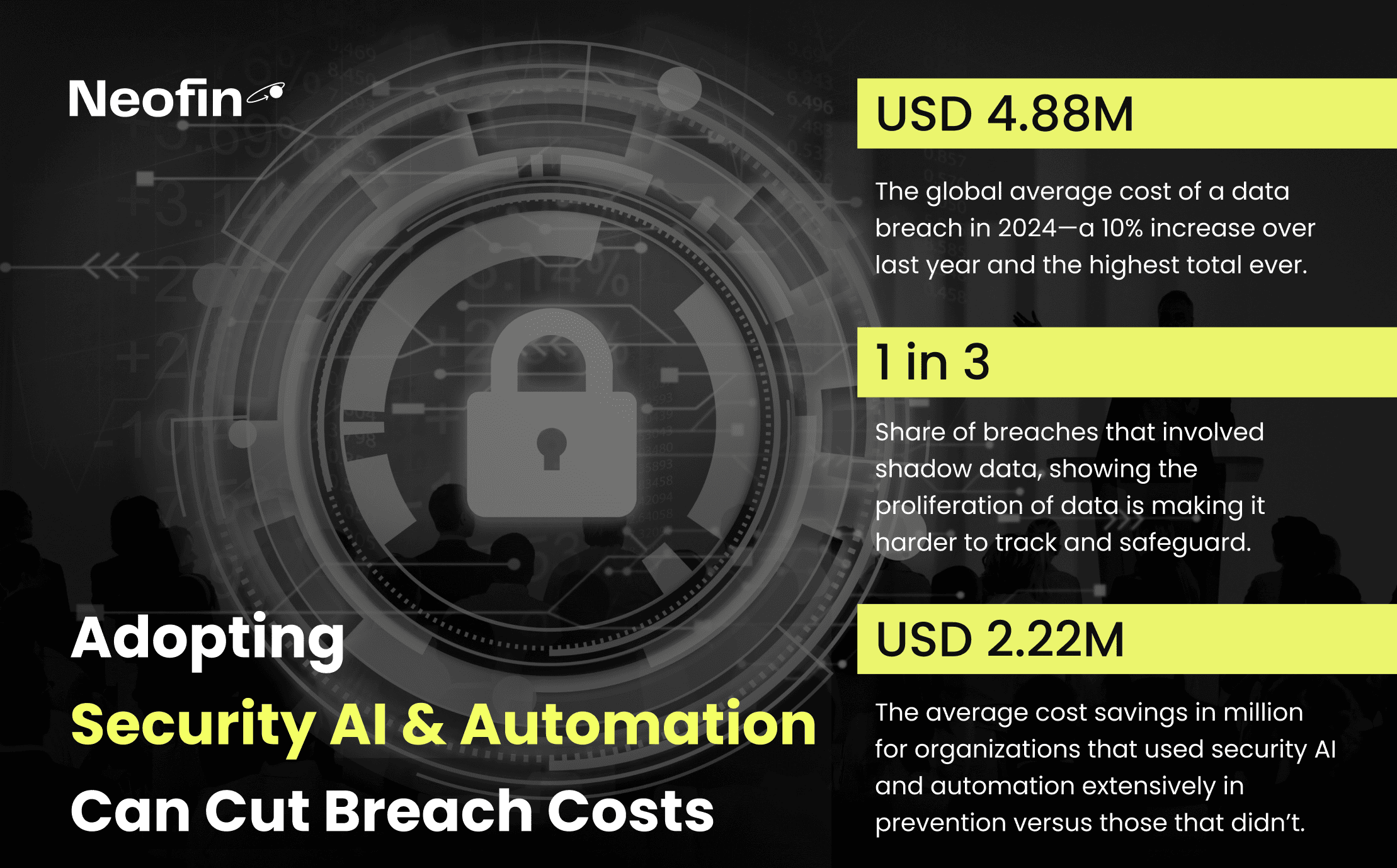
According to IBM’s Cost of a Data Breach Report, the global average cost of a breach surpasses $4 million, and that’s before considering lost business and reputational harm.
Data at Rest: Stored information, such as customer details, financial statements, and repayment records, are encrypted with robust algorithms like AES-256.
Data in Transit: All communications, from borrower to lender and between internal systems, use secure protocols like TLS 1.2+.
Best Practices for Encryption from Neofin
Encryption at Rest: Protects data stored in databases and backups.
Encryption in Transit: Secures data as it travels between servers, APIs, and end-users (TLS/SSL).
This end-to-end approach ensures that even if attackers intercept information, they can’t make sense of it.
Passwords alone are no match for determined cybercriminals. That’s where MFA steps in, adding extra layers, like SMS codes, authenticator apps, or fingerprint scans. If someone does steal a password, the second factor keeps the account locked down. This is particularly valuable for loan officers, underwriters, or customers who deal with big loans or sensitive financial data every day.
Beyond MFA, platforms should also streamline KYC (Know Your Customer) checks to root out fraudulent accounts. The last thing you want is approving a loan to a “ghost borrower.” We integrate these checks at Neofin to ensure that only legitimate users pass the front gate.
Best Practices for KYC from Neofin
At Neofin, we implement best-in-class KYC solutions to help lenders verify identities seamlessly while keeping the user experience smooth.
✅ Seamless Integration with Leading KYC Providers
We partner with Identomat, a global KYC provider, to deliver automated identity verification that meets compliance standards worldwide. Additionally, we integrate classic credit bureau data for enhanced verification, ensuring that every loan applicant is properly screened.
✅ Advanced Internal Security Features
Beyond third-party integrations, we also offer built-in solutions such as:
1. Liveness Detection. Prevents fraudsters from using stolen images or deepfake technology.
2. Face Comparison. Matches users’ real-time images with their official ID photos for secure identity confirmation.
Fraudsters don’t follow 9-to-5 schedules, and neither should your defense systems. AI-powered monitoring can analyze user behavior in real time, like spotting if someone is logging in from multiple locations at unusual hours or making suspiciously large loan applications back-to-back.
Neofin integrates with providers like Fingerprint.js (detecting malicious devices), Sanctions.io, and LexisNexis to cross-check suspicious users or transactions.
Behavioral analytics spot anomalies, like repeated high-value loans from a single IP, before fraud escalates.
The bottom line: you don’t just react to threats; you proactively lock them out before they do real damage.
Most data breaches are not the result of cinematic hacking scenes but rather simple misuse of internal privileges. Securities lending services involve multiple stakeholders, from traders to risk managers, and enforcing role-based access ensures only authorized personnel can modify or approve securities loans.
With Role-Based Access Control (RBAC), you grant employees access only to what they need to do their jobs, no more, no less. That “least privilege” principle drastically reduces human error and insider threats.
In practice, that means a collections agent doesn’t see the same sensitive data as an underwriter or a compliance officer. Audits become simpler, too: you know exactly who accessed what, and when.
Granular Privileges
A collections agent sees delinquent loans but not the full identity profiles of borrowers.
A compliance officer can generate AML reports but can’t edit or alter loan terms.
Our Insight: We use annual external audits to independently evaluate our policies on RBAC and confirm they align with best practices for the given moment. And in the platform, we solve this through the Administration engine that enables the permissions management and control.
Regulations are evolving nearly as fast as technology. Manually keeping tabs on every new rule can bury a team in admin work, not to mention the high risk of error. Automated compliance frameworks track changes in real-time, flag anomalies, and even generate regulatory reports automatically.

— Svitlanka Sergiichuk, Co-Founder at Neofin
Neofin’s system automatically flags any transaction, customer profile, or loan application that appears on global sanctions lists, immediately alerting compliance officers for review. Lenders can also configure no-code underwriting rules in the Underwriting Studio, setting automated approvals or rejections based on risk scores, credit thresholds, or AML requirements, helping to maintain consistent decision-making across all loan types. In addition, the platform compiles and formats the necessary documentation for quarterly AML reports or local regulatory directives, greatly reducing administrative burdens and the likelihood of human error.
No modern lending platform stands alone; integrations with payment processors, credit bureaus, and external systems are standard. But every integration is a potential backdoor if not secured.
A strong API security framework typically revolves around OAuth 2.0 and JWT (JSON Web Tokens) for authentication and authorization. OAuth 2.0 validates the identity of requesting services, while JWT secures and signs each session token, reducing the risk of session hijacking or unauthorized data access. Beyond authentication, safeguards like rate limiting, input validation, and threat detection help to catch and block suspicious traffic before it evolves into a full-scale attack.
Our infrastructure takes these principles a step further by auto-generating secure API endpoints whenever a lender configures or updates a workflow. As soon as any change is made, these endpoints are refreshed in real time, so you never need to patch manual security loopholes. By weaving in best practices from the start, lending platforms can scale and integrate with confidence, knowing their APIs are locked down against malicious actors.
A secure lending platform is only as strong as its underlying cloud infrastructure. In a world where downtime can stall critical financial operations, multi-cloud deployment has become the go-to strategy for ensuring redundancy and minimizing service interruptions. By spreading workloads across multiple providers, platforms can keep running smoothly even if one cloud service experiences an outage or performance issue.
Automated backups and robust disaster recovery (DR) plans are equally crucial. Whether it’s a minor hardware failure or a major security incident, having the ability to instantly restore systems and data can mean the difference between a brief hiccup and a business-crippling event. Scheduled snapshots, periodic failover tests, and clearly defined DR protocols all contribute to a more resilient lending environment.
Neofin’s infrastructure goes a step further, providing 99.95%–99.99% uptime through a cluster-based architecture. Each customer operates on their own dedicated, single-tenant instance, ensuring that an issue affecting one client won’t cascade to anyone else. This design not only isolates risk but also simplifies maintenance and scaling. By focusing on secure cloud deployment and well-honed DR practices, lenders can offer reliable services that keep both regulators and borrowers confident in the platform’s stability.
Security isn’t a one-and-done affair; even the most robust lending platforms can develop blind spots over time. Penetration testing helps uncover these hidden vulnerabilities before bad actors can take advantage of them. Ethical hackers simulate real-world attack scenarios, ranging from credential stuffing to advanced injection techniques, on your APIs, databases, and internal systems. By identifying weak points early, you can apply fixes and patches long before a genuine breach has a chance to disrupt operations.
These tests also serve as a drill for your incident response protocols. For instance, if a pen test reveals critical access issues within an underwriting module, your team learns how to swiftly isolate and remediate the problem. Regularly scheduled testing ensures your platform’s defenses evolve in tandem with new features or third-party integrations. Ultimately, proactive penetration testing isn’t just about discovering flaws, it’s about continuously reinforcing the trust borrowers and partners place in your lending ecosystem.
In cybersecurity, complacency is the enemy. Threats evolve, and so must your defenses. Regular security audits ensure your policies, code, and architecture stay aligned with best practices.
Frequent Checkpoints
Monthly or Quarterly reviews of logs, firewall configurations, role assignments, and potential anomalies.
Independent audits confirm you’re meeting external standards, keeping regulators at bay.
Neofin’s Transparency
We share clear, concise audit findings to help you maintain your own internal risk management.
Ongoing security training for staff ensures that everyone in the chain, developers, support, and customers, remains vigilant.
When you treat security as an ongoing commitment rather than a one-off milestone, you create a culture of trust, both internally and with your borrowers.
To conclude, in the world of digital lending, security isn’t just a feature — it’s a foundation. A single vulnerability can mean financial loss, regulatory penalties, or worst of all, broken trust. That’s why security needs to be proactive, layered, and continuously evolving.
From regulatory compliance and encryption to AI-powered fraud detection, the best lending platforms don’t just react to threats. They anticipate and prevent them. Security is never a one-and-done task; it requires constant vigilance, testing, and adaptation to stay ahead of emerging risks.
By embedding these 10 essential security features into your lending platform, you’re creating an ecosystem where innovation and security go hand in hand.
Would you like to dive deeper into any of these areas? Let’s start the conversation